Background
CI/CD is a DevOps practice aimed at streamlining the process of integrating code changes and delivering them to users. Kubernetes, being the de facto standard for container orchestration, is often the target deployment platform. Integrating CI/CD with Kubernetes ensures that updates to microservices and infrastructure can be tested, validated, and released automatically.
Traditional CI/CD pipelines were designed for static infrastructure. Kubernetes, with its dynamic and declarative nature, requires pipelines to interact with APIs, manage manifests, handle rolling updates, and ensure that the cluster state matches the desired state defined in version-controlled code.
Why It Matters
Deploying applications manually into Kubernetes is error-prone and does not scale. A CI/CD pipeline:
- Reduces deployment risk with automation and consistency
- Enables rapid delivery of features and fixes
- Supports collaboration across teams through version control and standardized workflows
- Allows for fast feedback loops via automated testing and monitoring
CI/CD is critical in Kubernetes environments where multiple services, teams, and environments (e.g., dev, staging, production) must be managed efficiently.
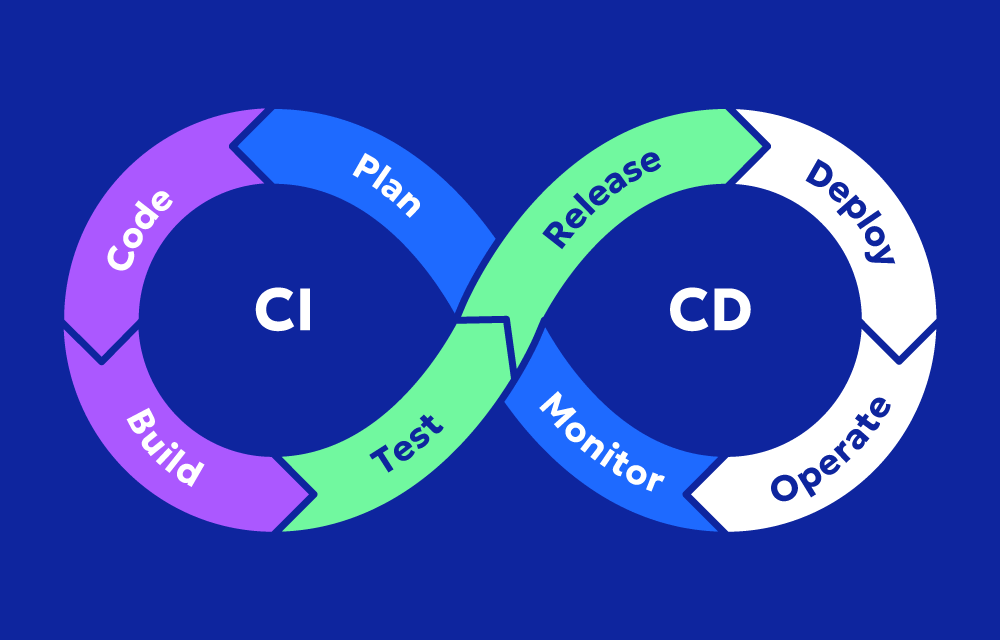
Components of a CI/CD Pipeline for Kubernetes
1. Source Control Integration
- Connects to a Git repository (e.g., GitHub, GitLab, Bitbucket)
- Triggers the pipeline on pull requests or merges
2. Build Stage
- Compiles code
- Builds container images (usually using Docker or BuildKit)
- Tags and pushes images to a container registry (e.g., Docker Hub, ECR, GCR)
3. Test Stage
- Runs unit, integration, and end-to-end tests
- Optionally runs security scans and linters (e.g., Trivy, SonarQube)
4. Deploy Stage
- Applies Kubernetes manifests using tools like
kubectl,Kustomize, or Helm - May use GitOps tools like Argo CD or Flux for declarative delivery
- Performs rolling updates or blue-green/canary deployments
5. Monitoring and Feedback
- Integrates with observability tools (e.g., Prometheus, Grafana, Loki)
- Sends alerts or logs pipeline success/failure
- Measures deployment health and rollout success
Example Pipeline (Using GitHub Actions + kubectl)
name: CI/CD Pipeline
on:
push:
branches: [ main ]
jobs:
build-and-deploy:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Build Docker image
run: docker build -t myapp:${{ github.sha }} .
- name: Push to Docker Hub
run: docker push myapp:${{ github.sha }}
- name: Deploy to K8s
run: |
kubectl set image deployment/myapp myapp=myapp:${{ github.sha }}
kubectl rollout status deployment/myapp
Best Practices
- Use declarative manifests in version control (e.g., YAML files for Deployments, Services)
- Isolate environments (dev/staging/prod) using namespaces or separate clusters
- Validate manifests with tools like
kubeval,conftest, orOPA - Automate rollback on failed deployments (e.g., using health checks and liveness probes)
- Secure the pipeline (limit access to kubeconfig, use secrets management for credentials)
Tools Commonly Used in Kubernetes CI/CD
- CI servers: GitHub Actions, GitLab CI, Jenkins, CircleCI
- Image builders: Docker, Kaniko, BuildKit
- Deployment: kubectl, Helm, Kustomize, Skaffold
- GitOps: Argo CD, Flux CD
- Security: Trivy, Aqua, Snyk
- Monitoring: Prometheus, Grafana, Datadog, Loki
Challenges
- Managing secrets securely across stages
- Dealing with flaky tests or unstable environments
- Scaling pipelines across many microservices
- Synchronizing deployments in multi-cluster setups
- Handling drift between Git and live Kubernetes state
Value Proposition
CI/CD pipelines in Kubernetes bring velocity, consistency, and confidence to software delivery. They allow developers to ship changes frequently and safely, reducing time to market and improving system resilience.
For organizations running critical workloads on Kubernetes, a robust CI/CD strategy is foundational to reliability and scalability.
Related Concepts
- GitOps: Managing deployments through Git as the single source of truth
- Infrastructure as Code (IaC): Declarative infrastructure definitions (e.g., Terraform, Crossplane)
- DevSecOps: Integrating security checks into CI/CD workflows
- Progressive delivery: Canary, blue-green, and feature flag-based rollouts