Introduction
Kubernetes schedules workloads across nodes based on resource availability and constraints. But what if you want to prevent certain workloads from running on specific nodes? That’s where Taints and Tolerations come in.
What Are Taints and Tolerations?
In Kubernetes:
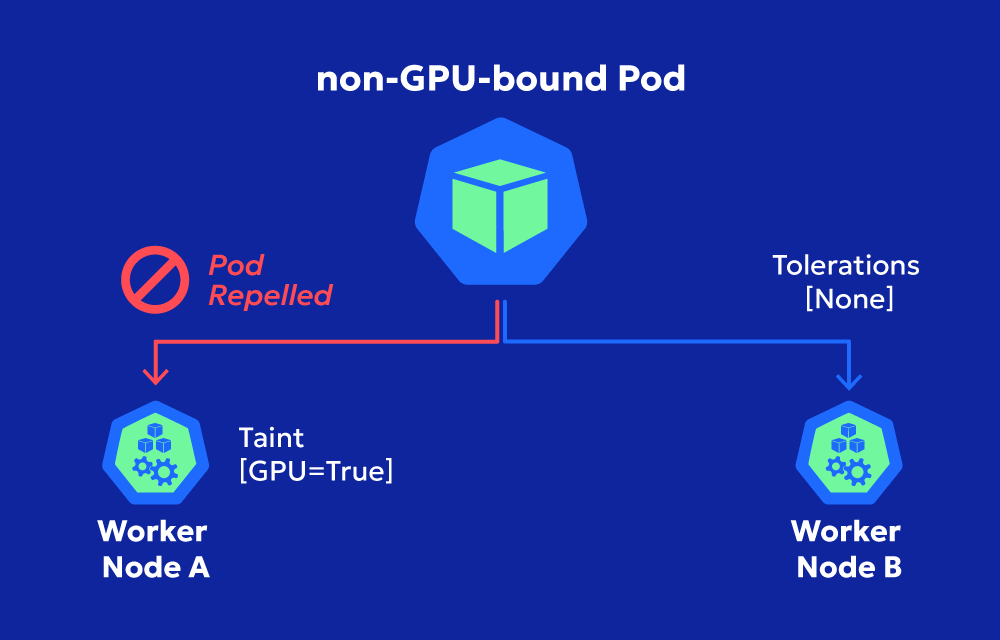
- Taints are applied to nodes to repel specific pods unless those pods have a matching toleration.
- Tolerations are applied to pods, allowing them to bypass taints and run on tainted nodes.
Taints prevent unwanted workloads from running on certain nodes, while tolerations enable exceptions when necessary.
How Taints Work
A taint consists of three components:
- Key: A label that identifies the taint.
- Value: An optional value for additional classification.
- Effect: Defines how the taint influences pod scheduling.
Kubernetes supports three taint effects:
NoSchedule→ Prevents pods from being scheduled on the node unless they have a matching toleration.PreferNoSchedule→ Softly discourages scheduling pods on the node but does not enforce it.NoExecute→ Immediately evicts existing pods unless they have a matching toleration.
Example: Applying a Taint to a Node
To apply a taint to a node, run:
kubectl taint nodes node-name key=value:NoSchedule
This command marks node-name with a taint that prevents pod scheduling unless they have the corresponding toleration.
How Tolerations Work
Tolerations allow specific pods to bypass taints and run on tainted nodes. They must match the key, value, and effect of a taint to be considered valid.
Example: Adding a Toleration to a Pod
Define a toleration in a pod specification:
apiVersion: v1
kind: Pod
metadata:
name: tolerant-pod
spec:
tolerations:
- key: "key"
operator: "Equal"
value: "value"
effect: "NoSchedule"
containers:
- name: app-container
image: nginx
This allows the pod to be scheduled on nodes tainted with key=value:NoSchedule.
Why Use Taints and Tolerations?
- Enforce workload isolation: Keep critical applications on dedicated nodes.
- Optimize resource allocation: Ensure high-priority workloads have exclusive access to specific resources.
- Improve cluster security: Prevent sensitive workloads from running on shared infrastructure.
- Manage heterogeneous clusters: Segregate workloads based on hardware type, compliance requirements, or performance needs.
Common Use Cases
Dedicated Nodes for Specific Applications
- Keep workloads like databases or GPU-intensive tasks on separate nodes by tainting general-purpose nodes.
Isolating System and User Workloads
- Prevent user applications from running on control plane nodes.
Handling Spot and On-Demand Instances
- Taint Spot Instance nodes (
spot=true:NoSchedule) to ensure only tolerant workloads use them.
Node Maintenance and Decommissioning
- Taint nodes (
maintenance=true:NoExecute) to evict all workloads before taking a node down.
Best Practices for Using Taints and Tolerations
- Use NoSchedule selectively – Prevent unwanted workloads without over-restricting scheduling.
- Pair with Node Affinity – Use Taints alongside Node Affinity for fine-grained scheduling control.
- Monitor eviction risks – Avoid NoExecute taints unless necessary, as they forcibly remove pods.
- Regularly review taints – Keep your cluster efficient by re-evaluating which nodes should remain tainted.
Final Thoughts
Taints and Tolerations are powerful tools for controlling workload placement in Kubernetes. Whether you need node isolation, workload prioritization, or security enforcement, these features help manage your cluster more effectively.
🚀 Next step? Try applying taints and tolerations in your Kubernetes cluster to optimize scheduling and resource allocation. Want to learn more? Check out the official Kubernetes documentation.