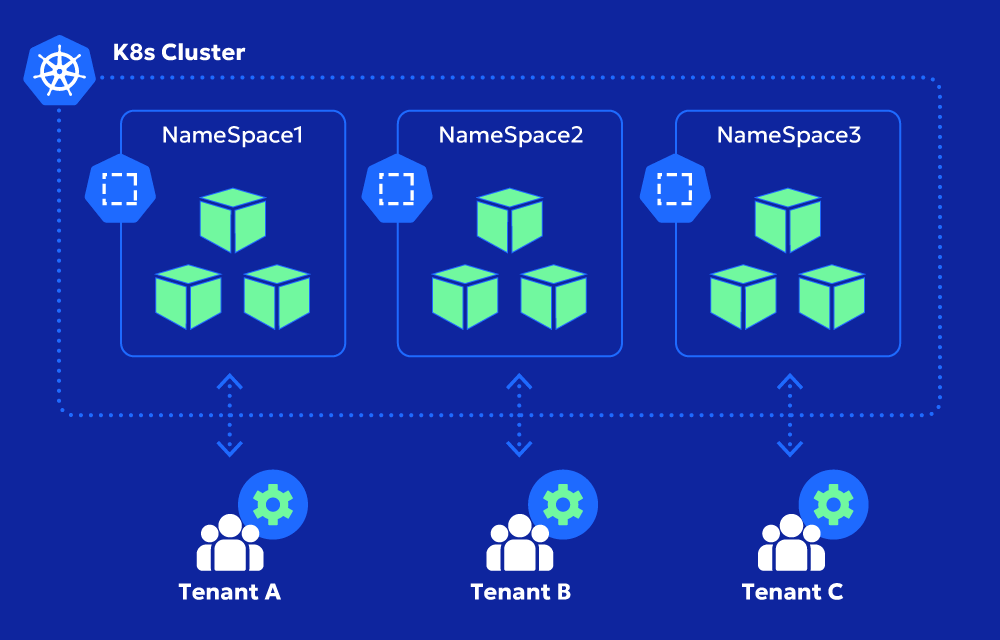
Think of it like an apartment building: each tenant (team or application) has their own space, but they all share the same building, security systems, and utilities. The key challenge is ensuring that no tenant can peek into another’s unit or take up more than their fair share of resources.
What is it used for?
Why use a multi-tenant cluster instead of separate clusters? It all comes down to efficiency:
- Lower Costs – Running a single cluster reduces infrastructure expenses compared to managing multiple clusters.
- Easier Management – A single control plane simplifies operations, monitoring, and governance.
- Resource Optimization – Resources like nodes and networking components are shared, minimizing waste.
- Faster Deployments – Teams can deploy applications without waiting for new clusters to be provisioned.
But it’s not all smooth sailing. Security, isolation, and fair resource distribution need to be carefully managed.
Challenges of Running a Multi-Tenant Cluster
1. Security & Isolation
When multiple teams or applications share a cluster, strict boundaries must be enforced to prevent accidental (or malicious) access to another tenant’s workloads. Key security measures include:
- Namespaces – Used to logically separate workloads.
- RBAC (Role-Based Access Control) – Defines who can do what within the cluster.
- Network Policies – Prevent cross-tenant communication unless explicitly allowed.
- Pod Security Standards (PSS) – Restrict what pods can do, limiting privilege escalation risks.
2. Resource Allocation & Fair Usage
Without proper limits, one tenant can hog CPU and memory, starving others. Kubernetes offers:
- Resource Requests & Limits – Ensures each tenant gets a fair share of CPU and memory.
- ResourceQuotas – Caps how much a namespace can consume.
- LimitRanges – Enforces min/max resource usage per container.
- Priority Classes & Preemption – Ensures critical workloads aren’t pushed aside by less important ones.
3. Network Segmentation
By default, all pods in a cluster can communicate. In a multi-tenant setup, that’s a security nightmare. Solutions include:
- Network Policies – Limit which pods can talk to each other.
- Dedicated Virtual Networks – Advanced setups use separate network layers for each tenant.
- Service Mesh (e.g., Istio, Linkerd) – Adds fine-grained traffic control and security.
4. Compliance & Governance
Regulated industries (finance, healthcare) need strong compliance controls. To meet security and audit requirements:
- Audit Logs – Track every action in the cluster.
- Policy Enforcement (e.g., Kyverno, OPA/Gatekeeper) – Prevents misconfigurations.
- Tenant-Level Monitoring – Ensures visibility into performance and security issues per tenant.
How to Implement Multi-Tenancy in Kubernetes
1. Soft Multi-Tenancy
- Uses Namespaces, RBAC, and Network Policies for separation.
- More lightweight but less secure (risk of accidental cross-tenant access).
2. Hard Multi-Tenancy
- Enforces strict isolation with Virtual Clusters (vClusters), separate node pools, or physical separation.
- More secure but requires extra operational complexity.
The right approach depends on your security needs and how much operational effort you’re willing to invest.
Popular Tools for Managing Multi-Tenant Clusters
- Capsule – A Kubernetes multi-tenancy framework for managing tenant isolation.
- vCluster – Creates virtual clusters inside a shared Kubernetes cluster.
- Kyverno / OPA – Policy engines to enforce tenant-specific rules.
- Calico / Cilium – Advanced network security for multi-tenant environments.